FBI Rings Alarm As DeFi Hacks Dominate Crypto Crimes: $1.3B Stolen In Q1 2022
2022.08.31 15:18
DeFi hacks have become so rampant that the FBI issued a warning to crypto investors. The agency cited a Chainalysis report from April, showing that cybercriminals stole $1.3 billion in cryptocurrencies in the first three months of 2022.
This is a 71% increase from 2021, and 97% of all crypto exploits involved DeFi platforms.
Unlike conservative Bitcoin, decentralized finance runs on more flexible and diverse smart contracts. This flexibility seemingly comes at the cost of security. What types of DeFi platforms are particularly at risk, and what does the FBI recommend to developers and investors?
The Most Common DeFi Exploits FBI Detected
Over the last decade, the FBI has continually expanded its Cyber Division. It has over 1,000 cyber security specialists across 56 field offices this year. In yesterday’s PSA, the FBI invited crypto investors to report cybercrime to their local office by filling out the Internet Crime Complaint Center (IC3) form.
In the PSA, the agency summed up all the typical cryptocurrency scams and DeFi exploits that the Tokenist has covered for years: flash loans, token bridge exploits, and token pair exploits. The latter involves price manipulation on DEXes by exploiting smart contracts in charge of slippage checks.
Slippage happens in token pair liquidity pools, such as ETH/WBTC, when the price of tokens varies between submitted and validated transactions. Attackers can exploit poorly coded slippage checks and bypass them with leveraged trades.
The resulting price calculation error then allows exploiters to drain liquidity pools. However, the FBI noted only $35 million lost in these types of exploits, completely overshadowed by the other two.
Flash Loans
Flash loans represent a blockchain novelty that was previously impossible, introduced in January 2020. By using smart contracts, a borrower can issue and pay back a loan within the same transaction (data block). If the borrower fails to pay it back instantly, the transaction reverses, as if the loan was never issued.
While not useful for common loan purposes, flash loans are critical for daily traders who amplify their positions when engaging with arbitrage opportunities. Typically, hackers exploit poor coding to buy enough crypto assets to trigger selloffs without having to put up collateral first. With the token’s price suppressed, they go to another DEX to sell it for a profit.
In April, hackers used this method to pilfer $182 million from Beanstalk Farms. The platform issues algorithmic stablecoin BEAN but uses credit instead of collateral to back it up. Because the platform is decentralized, buying tokens means buying voting power, which allowed hackers (exploiters) to change the governance rules and drain $182 million.
After the funds drained, the peg collapsed but stabilized later in August. The Bean team even begged the exploiter to return funds and keep 10% as a white hat (ethical hacker) bounty.
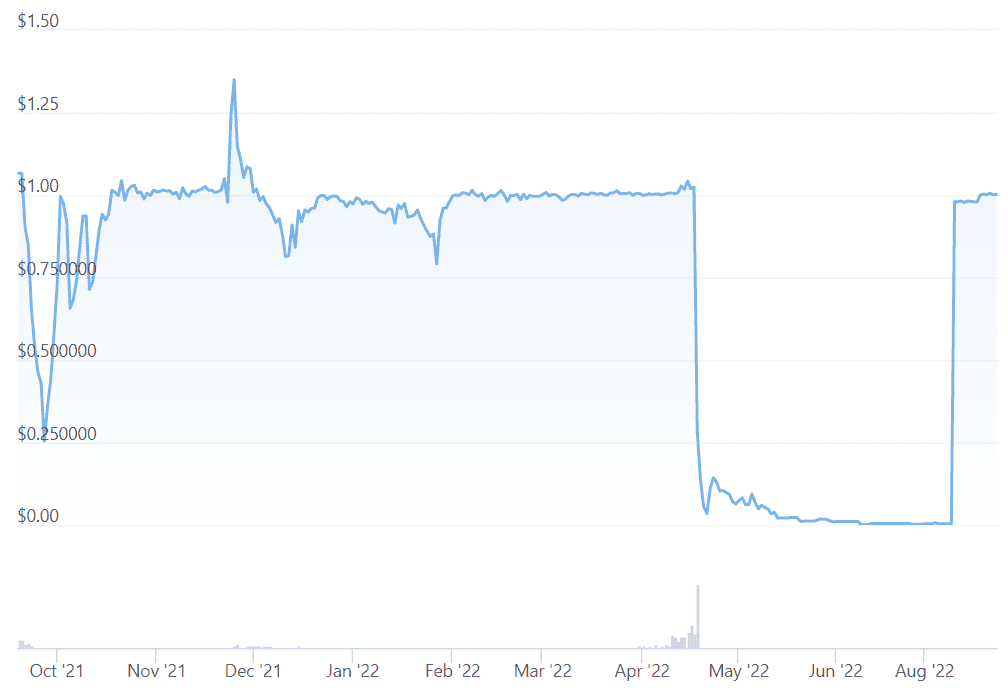 Collapse of BEAN stablecoin.
Collapse of BEAN stablecoin.
In July, Solana-based Nirvana Finance suffered $3.5 million in damage from a flash loan attack involving algorithmic stablecoin, NIRV. This year alone, over 17 such attacks occurred on various DeFi platforms.
Token Bridge Exploits
Because every blockchain network has its own governance rules, validators, and even smart contract standards, transferring digital assets from one to another is problematic. This is where blockchain bridges come into play. They are protocols running conversion smart contracts, so a token from one blockchain can be sent to another.
For example, if one were to use Bitcoin on Ethereum’s dApp as collateral, BTC would first have to be made compatible with Ethereum’s ERC-20 token standard. In charge of this conversion is a cross-chain smart contract like Binance Bridge.
The user would simply deposit bitcoins, and the bridge’s smart contract would convert them into Wrapped Bitcoin (wBTC). This way, newly minted wBTC is equal to the value of deposited BTC and tied to the same price moves, but is imbued with ERC-20 token functionality and compatibility.
Similarly, decentralized protocols like Zapper or Celer, can be used to send funds across dozens of different blockchain networks. The problem is that these token bridges serve as repositories, i.e., central points of failure. Surprisingly, the FBI failed to cite the latest Chainalysis report from August, which shows that token bridge attacks account for 69% of total stolen funds this year.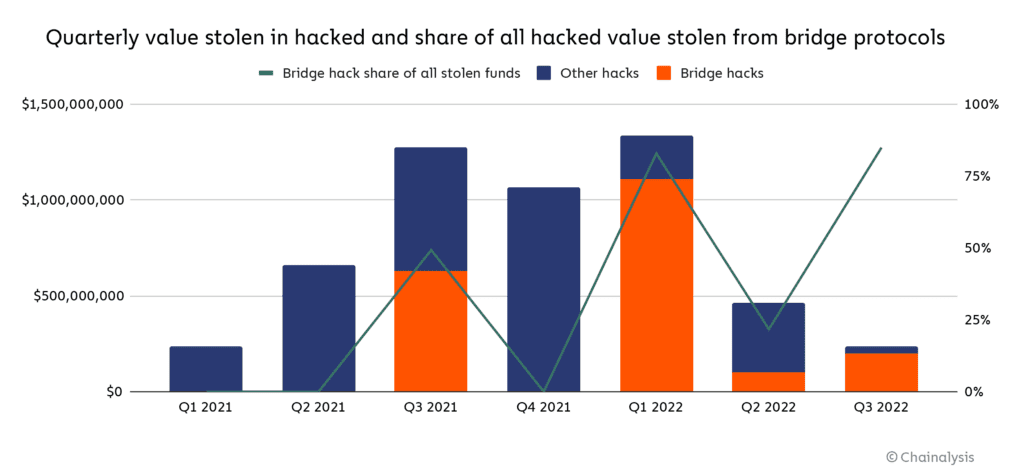 Chainalysis reported up to $2 billion stolen.
Chainalysis reported up to $2 billion stolen.
On August 2nd, attackers exploited the Nomad bridge smart contract, having drained nearly $200 million. Tom Robinson, from Elliptic blockchain security firm, noted that cross-chain bridges represent the least secure part of the blockchain infrastructure.
The record holder is still the Ronin Bridge hack, linking Axie Infinity’s Ronin sidechain to Ethereum. North Korean hackers stole $600 million worth of ETH and USDC stablecoins from it. Furthermore, Elliptic reported that open-source RenBridge has been (ab)used to launder up to $540 million in crypto funds, out of which $153 was for ransomware payments.
FBI’s Recommendations to Avoid DeFi Birthing Pains
DeFi investors are finding themselves between a rock and a hard place. On the one hand, everyone knows that the early bird gets the hyper-appreciated token later on. After all, this is how Ethereum went from under $1 billion in February 2020 to $111 billion TVL in November 2021.
On the other hand, new DeFi projects are in a hurry to tap into the FOMO growth, often de-prioritizing security and best coding practices. For this reason, the FBI encourages investors to take responsibility and research each project before diving in.
A part of that research is determining if the platform conducted independent code audits to identify smart contract vulnerabilities. In the case of the Ronin Bridge hack, Sky Mavis opened the bridge after two external audits by Verichains and Certik, and one internal one. Moreover, the fewer validators a protocol has, the more open it is for an exploit, which is why Sky Mavis is increasing its validator pool to 21 from the previous 5 – 9.
The FBI also mentions rapidly deployed platforms as a red flag. The agency doesn’t go into much detail, but a perfect example of a fraudulent DeFi project trying to ape the success of a legit one, was last week’s SudoRare $815k heist.
Lastly, the FBI recommends a prompt alert system for both developers and DeFi investors. In this vein, it would be prudent to follow Elliptic and Peckshield. These blockchain security companies often alert ongoing vulnerabilities or retweet others.






