Bitcoin vs. the quantum computer threat: Timeline and solutions (2025–2035)
2025.01.15 11:30
|
|
Recent breakthroughs in quantum computing have led market commentators to, once again, claim that Bitcoin’s future is under threat.
Google’s Willow quantum chip and its ability to significantly reduce the number of errors as it scales up the number of qubits are the newest source of generating fear, uncertainty and doubt about the prospects of Bitcoin’s survival in a post-quantum computing world.
The key concern is that a sufficiently advanced quantum computer will be able to break various forms of cryptography used in Bitcoin (and many other cryptocurrencies), effectively making the system unusable and worthless. For example, someone could attack the network with a 51% attack by mining with a quantum computer or steal coins held in addresses by more easily guessing the private keys associated with them.
So, is this a genuine and imminent threat? And what can developers do, if required, to fix this much-discussed issue?
According to longtime Bitcoin researcher Ethan Heilman, keeping Bitcoin’s cryptography secure from quantum computers and other potential threats will be a never-ending battle for developers.
“Bitcoin needs to protect people’s funds over generational timescales,” Heilman tells Magazine.
“The history of cryptography is one of change and adoption to new attacks, faster computers and better algorithms. So, the grand challenge for those working on Bitcoin cryptography is: How do you protect coins over decades or even centuries, given the mercurial nature of cryptographic security?”
Is Google’s Willow quantum computer a threat to Bitcoin in 2024?
The first thing to note about the potential threat quantum computers pose to Bitcoin is that the issue is completely overblown at this time. Willow is one of the frontrunners in quantum computing built up to this point, but it’s nowhere near what would be needed to threaten the cryptography used in Bitcoin.

 Willow marketing image. (Google)
Willow marketing image. (Google)
According to a 2022 research study by Universal Quantum, which is a spin-off company associated with the University of Sussex, a quantum computer with 13 million qubits would take a day to crack a private key associated with a vulnerable Bitcoin address. Google’s Willow only has 105 qubits.
Indeed, Google themselves told The Verge that Willow is not a threat to modern cryptography. Additionally, Nvidia CEO Jensen Huang stated that “very useful quantum computers” are probably still twenty years away, which implies their real world applications will be limited for some time.
On a recent episode of ARK Invest’s Bitcoin Brainstorm podcast, Blockstream co-founder and CEO Adam Back also pushed back on those claiming the quantum threat to Bitcoin is imminent.
“It’s kind of tempting to propose a bet to some of them because they’re saying that we should watch out by 2028—like, no way,” he said.

 The gang talks quantum computers and Bitcoin. (ARK Invest/YouTube)
The gang talks quantum computers and Bitcoin. (ARK Invest/YouTube)
However, the potential threat posed to Bitcoin by quantum computing has been a known issue for a long time, and discussions around it — or at least discussions around the theoretical breaking of SHA-256 algorithm used in the mining process — date all the way back to a time when Bitcoin creator Satoshi Nakamoto was still involved in the project. Upgrades to quantum-resistant Bitcoin addresses or other alterations to the cryptography used in Bitcoin can be implemented when needed.
As a side note, this is far from a Bitcoin-only problem, as the cryptography used in the traditional banking system is also vulnerable to attacks from quantum computers and currently poses a much bigger target.
When will quantum computers break Bitcoin? Expert predictions for 2030–2035
Bitcoin developers and other interest parties are generally skeptical and cautious about the potential threat.
“I just want to make sure that we’re thinking about this correctly,” said ARK Invest CEO Cathie Wood on the recent quantum computing-focused episode of Bitcoin Brainstorm.
“I don’t want to dismiss any possibilities because I do think technologies are moving ahead faster and faster.”
While there are still a fairly large number of different innovations that need to be made in quantum computing for it to become a serious threat to Bitcoin, it makes sense to start discussing the issue more seriously today.
Read also
Features
How the digital yuan could change the world… for better or worse
Features
Wild, Wild East: Why the ICO Boom in China Refuses to Die
Most estimates do not see quantum computing as a threat to the cryptography used in Bitcoin until the 2030s at the earliest. Notably, the National Institute for Standards and Technology (NIST) recommends migrating to new cryptographic systems by 2035 to mitigate forward-secrecy risks related to future quantum threats. However, Bitcoin would still be safe under this level of threat, as it is not impacted by forward secrecy risks, according to Ledger chief technology officer Charles Guillemet.
Additionally, IBM’s quantum computing roadmap points to a few thousand qubits by 2033. That’s still far short of the millions of qubits likely needed to break the cryptography in Bitcoin.
Analysts from Bernstein still see the quantum threat to Bitcoin as decades away.
Indeed, the estimates from Bitcoin developers and industry personnel in terms of when quantum computing will pose a genuine threat range are wide, and some refer to quantum computing as an outright scam. In a recent discussion on quantum resistance on the Bitcoin Development Mailing List, estimates ranged from a decade or two to “not in my lifetime.”
Despite this, there is a growing call for the issue to be taken seriously right now, as recent advancements indicate further progress may just be a matter of time at this point. “I think today the message needs to be: yes, unequivocally, worry about this now,” theoretical computer scientist Scott Aaronson recently wrote. “Have a plan.”
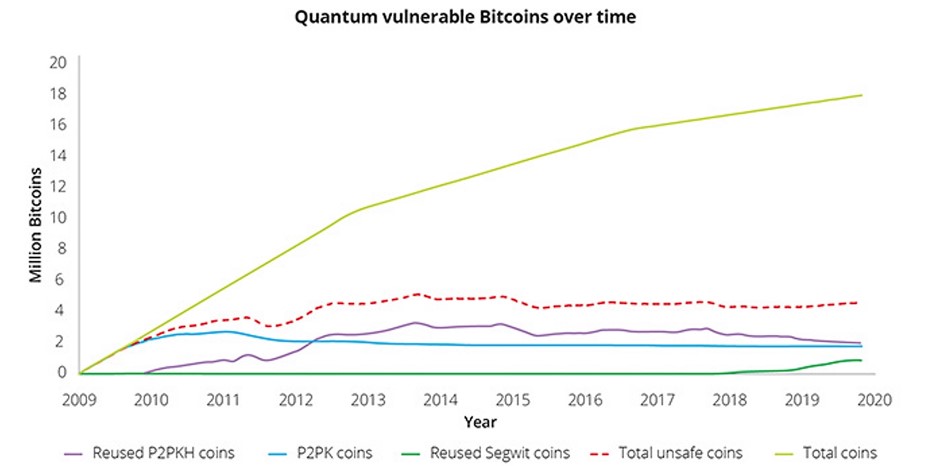
 The total number of unsafe Bitcoin is not as great as you might think. (Deloitte)
The total number of unsafe Bitcoin is not as great as you might think. (Deloitte)
The good news is that around 75% of all Bitcoin wallets are already safe from potential attacks due to the type of Bitcoin address they are stored in, according to a previous study from accounting giant Deloitte. Specifically, P2PK addresses and reused P2PKH addresses are the types of addresses that are vulnerable to quantum attacks. Of course, non-reused P2PKH addresses would also become vulnerable as quantum computers become more powerful because their signed transactions can be viewed in the mempool before they are confirmed (assuming the transactions aren’t made out of band and sent directly to a miner).
That said, there is already at least one in-development proposal for upgrading Bitcoin to address this threat.
Bitcoin’s quantum resistance: Current protection and future solutions
There are two key areas of concern around algorithms that are built specifically for use with quantum computers that give them massive gains over current methods for breaking encryption found with traditional computers.
One of these is called Grover’s algorithm and could be used via a quantum computer to gain an insurmountable advantage in the Bitcoin mining process and completely centralize Bitcoin’s accounting system to the point where the network can effectively be attacked or censored via a 51% attack. Secondly, Shor’s algorithm can be used on certain types of Bitcoin signature schemes to steal funds held in addresses. Shor’s algorithm provides exponential gains as compared to traditional methods and is the more immediate threat.
Notably, it is possible for Bitcoin wallets to prepare for the threat posed to Bitcoin address security today without having to make any changes to Bitcoin’s consensus rules, which is known to be a rather slow and difficult process. A soft fork would eventually be necessary to eventually activate a consensus rule change for quantum resistance on the network. However, preparations can be made long before any quantum threat to Bitcoin is apparent.
The process would be for wallets to start having an additional, quantum-secure signature scheme deployed in wallet software over the near term. Then, the nodes on the Bitcoin network could disable the previous, quantum-vulnerable signature schemes and require the new, quantum-resistant schemes to be used via a soft fork once the threat of quantum computers is imminent.
Read also
Features
Green consumers want supply chain transparency via blockchain
Features
How to prepare for the end of the bull run, Part 1: Timing
QuBit: Bitcoin’s proposed quantum-resistant upgrade explained
A draft Bitcoin Improvement Proposal (BIP) known as QuBit by the pseudonymous Hunter Beast introduces a new address type, Pay to Quantum Resistant Hash (P2QRH), which uses various quantum-resistant signature schemes to protect against attacks leveraging Shor’s algorithm. The new address type could come with a 16x discount in terms of block space costs, providing an economic incentive for users to move over to the quantum-resistant addresses. A similar economic incentive was previously used to promote the adoption of Segregated Witness addresses on the network.
The QuBit plan involves four stages: a quantum-resistant address standard, a Taproot-compatible quantum-resistant address standard, a soft fork and a quantum-secure address standard.
Hunter Beast’s work on P2QRH has been funded by Surmount Systems, which is an initiative to protect Bitcoin from potential threats related to quantum computing. P2QRH addresses make a quantum attack on a particular address uneconomical rather than impossible, similar to the role proof-of-work mining plays in Bitcoin.
According to Hunter Beast, making addresses fully quantum secure would require further deployment of quantum computing hardware among Bitcoin users. However, this upgrade could also eventually be soft-forked in at a later date. Further protections for the mining process would be even further down the line and not viewed as a relevant consideration at this time.
 Meet the Quantum resistance. (GitHub/cryptoquick)
Meet the Quantum resistance. (GitHub/cryptoquick)
Notably, P2QRH does not implement a specific quantum-resistant hashing algorithm. Instead, users are able to choose from a few different supported standards, including SPHINCS+-256f and FALCON-1024. Quantum-resistant signature schemes are still relatively new and unproven, so it’s difficult to pin down the best option for integration into Bitcoin. Additionally, the most trusted signature schemes also tend to be the largest, which could introduce new scalability issues.
Alternative solutions: OP_CAT and STARK-based protection
There is also the potential for new opcodes, such as OP_CAT, which is a previously deactivated opcode that some developers would like to see reactivated on Bitcoin to enable quantum-resistant addresses on Bitcoin.
Blockstream’s Jonas Nick recently published code for an experimental tool that could be used to generate quantum-resistant signatures using opcodes that could potentially be reactivated via the Great Script Restoration proposal. However, like any change to Bitcoin, OP_CAT could be seen as controversial, and there are potential centralization concerns related to the enabling of maximum extractable value (MEV) associated with it.
“OP_CAT can be used to implement post-quantum cryptography on Bitcoin, but it would be horribly inefficient from a transaction size perspective,” Hunter Beast tells Magazine.
OP_CAT co-author Ethan Heilman agrees that Beast’s proposal is likely to be implemented before the problem arises. “Having OP_CAT deployed would be a helpful tool during a cryptographic crisis. That said, I think we should, and likely will, solve this problem with dedicated quantum resistant outputs, such as QuBit (BIP-360), well before any such crisis arises.”

 Bitcoin researcher Ethan Heilman. (LinkedIn)
Bitcoin researcher Ethan Heilman. (LinkedIn)
There are trade-offs made with QuBit, such as an effective lowering of Bitcoin’s onchain transaction capacity, but many consider this as more acceptable due to it acting as a strict security gain. Due to the larger size of quantum-resistant transactions, there have also been discussions around potentially combining the addition of quantum-resistant signatures with a block size increase.
There is also the possibility of using Scalable Transparent ARguments of Knowledge (STARKs), which is zero-knowledge (ZK) proof technology, as another route for bringing quantum resistance to Bitcoin, which would come with added privacy and scalability benefits. This functionality could be enabled via OP_CAT or another opcode specifically for verifying ZK-proofs.
“STARK support in Bitcoin could let miners non-interactively aggregate quantum resistant signatures into a single STARK, replacing the signatures with a single STARK,” Heilman told Magazine.
“This would eliminate the main drawback of such signature schemes and could also have privacy benefits. Many people, myself included, are looking into this, but this work is still early, and such changes are not very simple or easy.”
That said, STARKs are more practical for more flexible and malleable crypto systems, such as Ethereum or Solana. Indeed, Ethereum creator Vitalik Buterin has previously opined on the use of STARKs in a quantum emergency.
In terms of the potential of using STARKs or other methods for quantum computing resistance even for non-upgraded addresses (as Buterin has outlined), Hunter Beast states, “It might be possible . . . The only problem with this approach is that while adding ZK opcodes is a soft fork, there’ll likely be little agreement on which ones to add, and even if there is, for it to work. They would also need to disable all transactions that aren’t made with modern HD wallets (ones that accept mnemonic seeds and produce new addresses each time they’re used). A hardcoded private key won’t work, and it’s also uncertain how that would work with multisig. So, no, it’s not really practical to do that.”
Bitcoiners value stability and consistency, so change is likely to be slow and gradual. But with preparations already being made despite no clear threat, it’s likely this is an issue that can be dealt with in a timely fashion.
The reality of the potential threat quantum computing poses to Bitcoin was recently summarized well by Blockstream CEO Adam Back on X: “I think quantum readiness is the right balance – not like there is any current risk, nor likely for this decade, or probably the next,” said Back. “But being ready is ok.”
Subscribe
The most engaging reads in blockchain. Delivered once a
week.




Kyle Torpey
Kyle Torpey has been covering Bitcoin and crypto since 2014. Notably, he covered Bitcoin’s blocksize war at Bitcoin Magazine and Forbes. Over the years, his work has also been published in Fortune, Vice, Investopedia, and many other media outlets








